Secure Microsoft 365:
Advanced Threat Detection & Investigation for Microsoft 365
Proactively detect, investigate, and disrupt sophisticated threats targeting your Microsoft 365 environment with AI-powered security
Start Your Free TrialProactive Threat Detection in Microsoft 365
Automatically surface anomalies and threats within Microsoft 365 environments, allowing faster investigation of suspicious activity like privilege escalation, abnormal login patterns, or data exfiltration attempts.
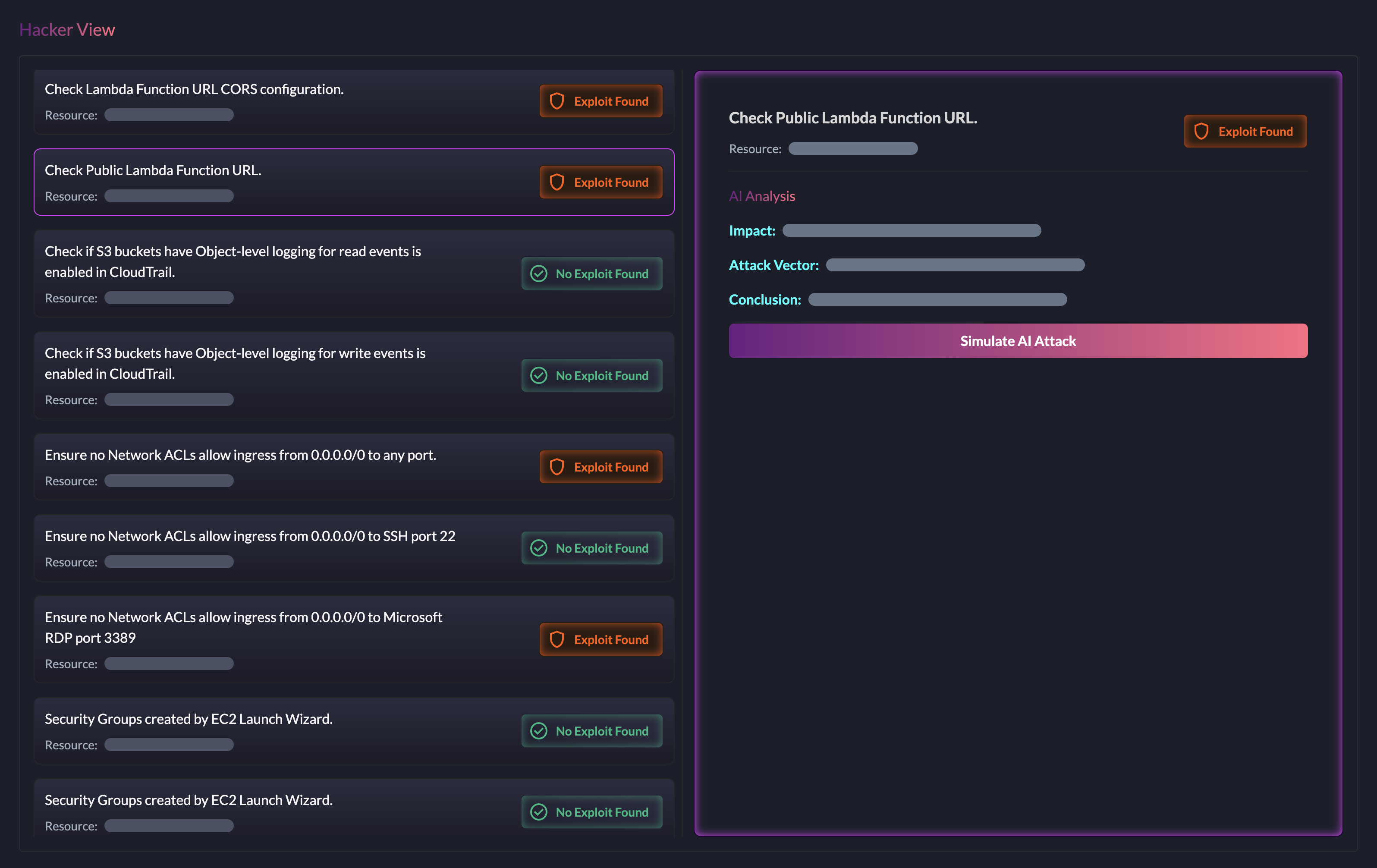
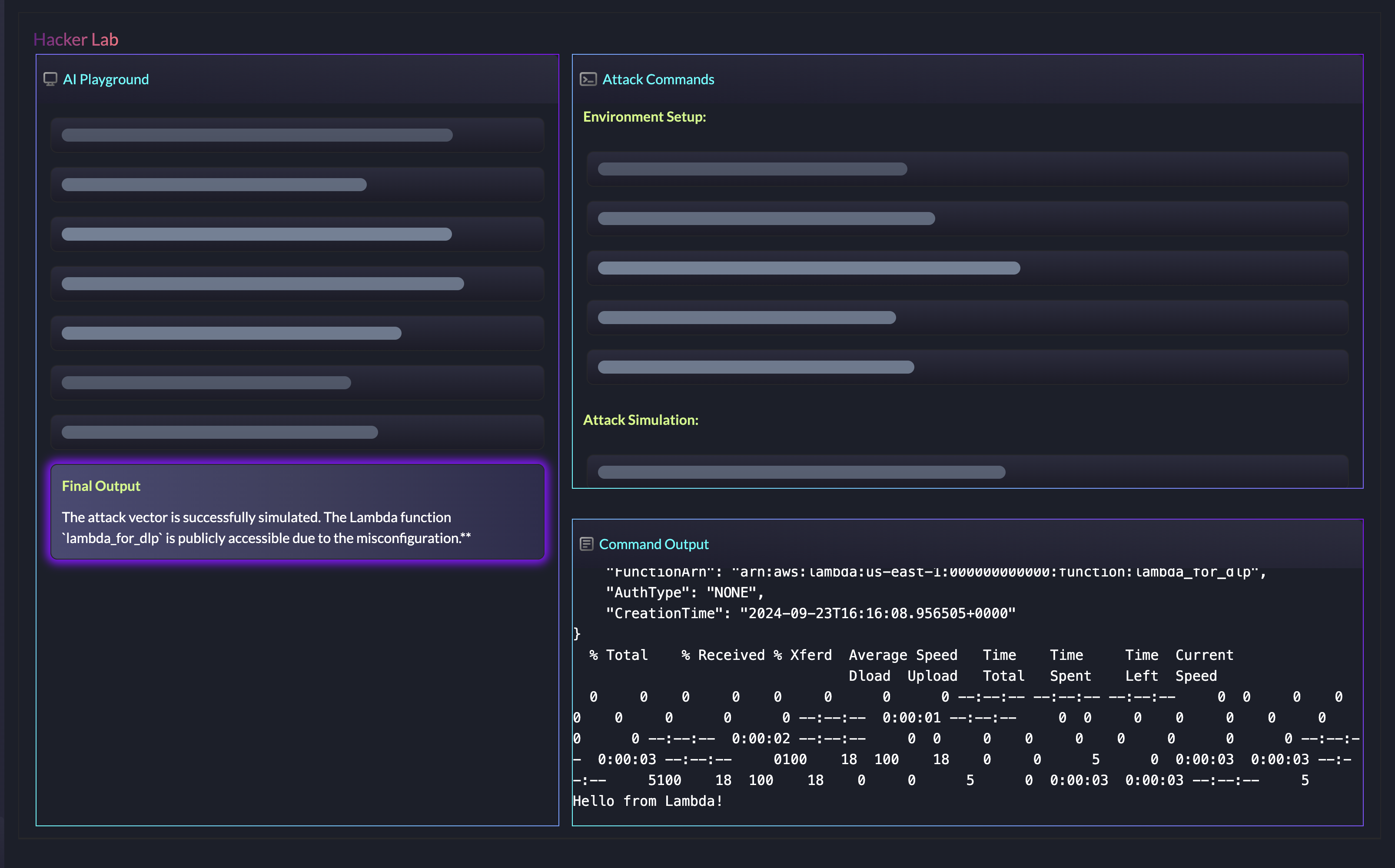
AI Attack Tracing
Secto’s AI traces the full attack sequence-linking reconnaissance, privilege abuse, lateral movement, and data exfiltration, to detect and analyze active threats in real time. It doesn’t stop at detection: Secto autonomously investigates and disrupts attacks, reducing response time and stopping threats before they escalate.
Key Features
Secto ensures cloud security best practices by leveraging AI-powered monitoring and Validations to continuously identify, prioritize, and remediate exploitable vulnerabilities.
Proactive Threat Detection in Microsoft 365
Automatically surface anomalies and threats within Microsoft 365 environments, allowing faster investigation of suspicious activity like privilege escalation, abnormal login patterns, or data exfiltration attempts.
Cloud Misconfiguration Detection
Continuous scanning of cloud infrastructure to identify critical misconfigurations across IAM, S3-equivalent storage, serverless functions, and virtual machines, helping prevent exploitable gaps before attackers can leverage them.
Attacker Tracing & Investigation
Secto's AI traces the full attack sequence-linking reconnaissance, privilege abuse, lateral movement, and data exfiltration, to detect and analyze active threats in real time. Advanced investigation capabilities provide detailed attack timelines and impact assessment for faster response.
Focused Security Efforts
Save time by addressing only truly exploitable vulnerabilities.
Actionable AI Insights
Offers AI insights and evidence on exploitation methods.
Attack Disruptions
Autonomously disrupt active threats in real-time, stopping attacks before they can cause damage or escalate further.
Our Pricing Plan
Our Microsoft 365 security platform is designed to empower you with advanced threat detection capabilities, making your security operations more efficient, accurate, and proactive.
Enterprise
CUSTOM
-
Enterprise-grade Security Platform
-
Custom integrations
-
Custom Deployment Options
-
Dedicated Account Management
No extra hidden charge
What Our User Says

Security Executive
Global Banking Organization
With Secto monitoring our Microsoft 365 environment, we've gained real-time visibility into complex threat patterns, including privilege escalations and data exfiltration. It helps us respond before attackers can impact our sensitive operations.

President
Regional MSP
Secto has transformed how we secure Microsoft 365 for our clients. The automated anomaly detection and response workflows eliminate manual overhead and give us confidence that even stealthy attacks won’t slip through the cracks.

Chief Technology Officer
IT Services and Solutions
With Secto integrated into our Microsoft 365 security stack, we’ve elevated threat visibility and response automation across our client environments. Its ability to detect misconfigurations, trace complex attack paths, and autonomously mitigate risks has greatly strengthened our service offerings.
Experience The Future of Cloud Security
Join forces with us to secure your cloud. Our expert team is prepared to assist with inquiries, assess your environment, and tailor our platform to meet your specific needs. Contact us now!